Students Hack Popular Device to Track Jogger's Whereabouts

A popular runner's device that combines Nike shoes with an iPod to track a workout could also be used by criminals to track a person's whereabouts.
In fact, the hack is so easy and sneaky that someone might already be doing it and no one would know.
The device, called Nike+iPod, employs a small computer chip in the shoe that beams data to a receiver attached to an iPod Nano. Some 450,000 of the $29 devices have been sold.
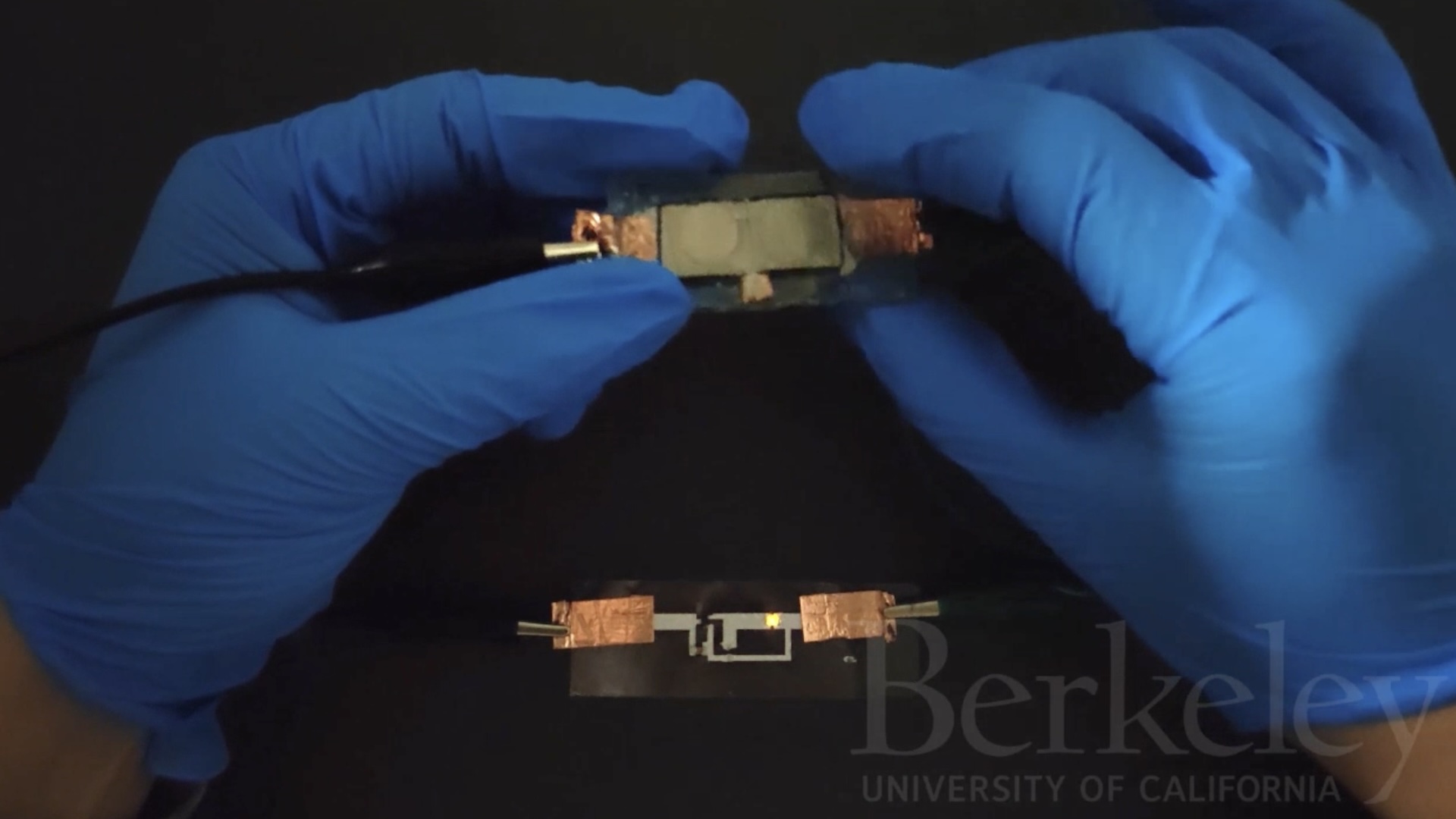
But the signal can be tracked up to 60 feet away, a group of computer science students has found. They built a simple device [image] for less than $300 that hacks into the runner's gear.
"It is easy for someone to use the Nike+iPod as a tracking device," says Scott Saponas, an avid runner and doctoral student in computer science at the University of Washington. "It's an example of how new gadgetry can erode our personal privacy."
Coupled with GoogleMaps, the potentially nefarious device—no bigger than a matchbox—could be used to track a person leaving their home, alerting a thief to the best time to do the obvious, Saponas and his colleagues warn.
Or a stalker could hide receivers near a home, a gym or other locations to closely monitor the target's movements. Hiding multiple devices on a college campus could result in a network that would report the data to a computer in a dorm room via a common campus-wide wireless network, Saponas points out. To computer geeks, the scheme is all basic stuff.
Sign up for the Live Science daily newsletter now
Get the world’s most fascinating discoveries delivered straight to your inbox.
The researchers say an electronics hobbyist as young as a middle-schooler with modest computer knowledge and the ability to solder could easily build one of these in a weekend.
"Because it's a passive listening technology, we don't know if there are other people already doing this," Saponas told LiveScience.
Protection is fairly simple: Just switch the device off. It is sold with the power on, and most users never bother to turn it off, the researchers say. They add that the Nike+iPod kit could have been made more secure if it used standard techniques from modern cryptography.
"There's a bigger issue here," said Yoshi Kohno, senior author on the paper the group has posted to its web site. "When people buy a toaster, they know it's probably not going to blow up when they plug it in. But when they buy a consumer device like the Nike+iPod kit, they have no idea whether the device might enable someone to violate their privacy. We need to change that."
- The Biggest Popular Myths
- Why We Walk and Run vs. Hopping and Skipping
- The First Runner's High: Jogging Separated Humans from Apes
- Family DNA Helps Cops Catch Criminals
- Life's Little Mysteries
Robert is an independent health and science journalist and writer based in Phoenix, Arizona. He is a former editor-in-chief of Live Science with over 20 years of experience as a reporter and editor. He has worked on websites such as Space.com and Tom's Guide, and is a contributor on Medium, covering how we age and how to optimize the mind and body through time. He has a journalism degree from Humboldt State University in California.