What Makes A 'Smart Gun' Smart?

This article was originally published at The Conversation.The publication contributed the article to Live Science's Expert Voices: Op-Ed & Insights.
Every time a toddler accidentally shoots a friend or family member, a teen kills himself via gunshot or a shooter perpetrates an act of mass violence, public discussion circles back to “smart gun” technology. The concept has roots in a 1995 National Institute of Justice (NIJ) study that recommended a technology-based approach to reduce the incidence of police officers killed in gun-grabs by assailants. More recently, President Obama’s message on gun violence included specific recommendations on federal actions designed to promote the development and commercialization of electronic gun-safety systems.
The term “smart gun” has been embraced by the popular press as a catchall for all forms of electronic personalized safety technology. The idea is to make sure a gun can be fired only by its authorized user. But the different scenarios in which a gun could be inappropriately discharged call for fundamentally different safety systems.
The metaphor of a common door lock is a useful way to think about the various technological approaches. The key serves as the personal identifier. The pin tumblers that recognize the key inside the lock serve as the authenticator. And the latch serves as the block. All electronic gun safety systems must accomplish all three of these basic functions – identify authorized shooters, authenticate their credentials and then release the block to the firing mechanism.
How one satisfies those needs is subject to the performance constraints of the application environment and the physical constraints of the weapon itself. These differences create distinct branches on the family tree of personalized-weapons technology.
Proximity sensors – can you hear me now?
One group of solutions owes its heritage to the NIJ study focused on protecting police weapons from takeaway during a close quarters struggle. It suggested a token-based proximity sensor using Radio Frequency Identification (RFID). A number of working RFID prototype guns have been demonstrated, beginning with Colt’s 1996 handgun and including Triggersmart, iGun M-2000 and the Armatix iP1.
In a badge, wristband or ring, a user wears a passive RFID tag, like those embedded in products to prevent shoplifting. It’s the “token” and serves as the key in the front door metaphor. Like a physical key, it can be duplicated or shared. What matters is possession of the token, not the identity of the token holder.
Sign up for the Live Science daily newsletter now
Get the world’s most fascinating discoveries delivered straight to your inbox.
A wireless RFID reader is built into the gun and serves the role of authenticator. It generates a signal that activates the RFID tag to respond with an embedded code. If there’s a match, the electromechanical components unblock the weapon firing system and the gun functions normally. The response time of these systems is generally dependent on the choice of electromechanical components used in the blocking system (e.g., servomotors, solenoids, shape memory metals), but are generally less than half a second. By design, the gun can remain active as long as there is a signal link, or in some configurations as long as pressure sensors detect the gun is being held.
If the tag is too far away from the transmitter to self-activate and respond, then it’s like losing your key to the front door – the gun remains locked down. The Armatix iP1, for example, specifies a range of 15 inches. If you try to spoof the transponder with a signal that does not contain the individual code, it’s like using the wrong key – it may fit the slot but cannot be turned because it does not match the tumblers – and the gun remains locked down.

Various designs interfere with the mechanical firing mechanism in different places – from trigger bar to firing pin. There are also different technologies including solenoid actuators, shape memory alloy-based components and even electronic firing systems that serve as the deadbolt to be released upon receiving an authentication system. The details are proprietary to the individual products on the market and reflect design trade-offs in power consumption, free space to accommodate components and response time.
Proximity of gun to token is not an absolute determinant of rightful possession during a close-quarters struggle. But the technology does offer simplicity of operation, easy weapons exchange across permitted users (i.e., partners) and reliably disables a weapon from use if the officer has been overpowered and the duty weapon taken.
Biometrics – do I know you?
The benefits of a token-based system in a street encounter become a liability in the home. The viability of the approach is wholly dependent on the owner securing the token where it cannot be accessed by denied users. But guns used for home protection are more likely to have token and weapon stored together to prevent any delay in the event of an intrusion. And anyone who has both the token and the weapon can fire it.
A second group of technologies evolved in response to child-safe handgun legislation adopted in New Jersey and Maryland in the early 2000s, designed to prevent unauthorized use of personal firearms stored in the home. Biometric authentication systems eliminate the physical token. Instead, a measurable physical characteristic of any authorized user becomes the key. It can’t be taken without permission, counterfeit or otherwise transferred.
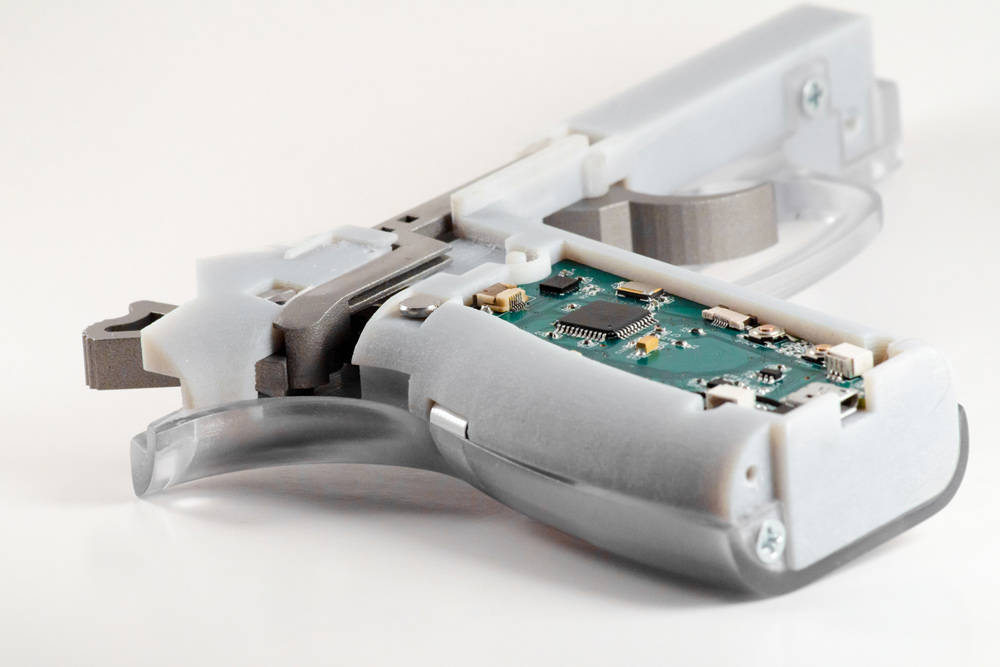
To date, fingerprints have been the primary attribute used in biometric systems. Kodiak Arms Intelligun and Safe Gun Technology’s retrofit for rifles use fingerprint detection as a primary mode of security. If the fingerprint is the key, then the sensor and pattern matching software are the pin tumblers that perform the authentication function in these guns.
The most widely used sensor technology relies on capacitance imaging of the fingerprint. The variation in distance between the ridges and grooves of the finger and the sensor plate creates a distribution of electrical charge storage (capacitance) that can be measured in an array of conductor plates in the sensor. Other fingerprint sensors rely on infrared (thermal) imaging, and some use pressure detection to create a digital pattern that is a unique representation of the print.
The sensor software needs to be trained to store acceptable patterns that may represent different fingers of a single user or various fingers from multiple authorized users. After that, any pattern that doesn’t match within some specified tolerance is rejected. The reliability of the authentication process is influenced by the resolution of the sensor, the extent and orientation of the exposed finger, and physical factors that can interfere with the mapping. For example, moisture on the finger can defeat a capacitive detector, cold fingers can reduce the reliability of thermal imaging, and dirt, paint or gloves can obscure the fingerprint beyond recognition.

There are other types of biometric security being explored. One prototype sponsored by NIJ adopted vascular biometrics that detect the blood vessel structure below the skin surface. An emerging class of biometrics are dynamic or behavioral and combine some element of individualized physicality amplified by learned patterns of behavior. For instance, voice identification combines the structure of one’s vocal chords with the breath patterns of speech learned in infancy. Electronic signature authentication captures the speed and pressure of pen on LCD pad (and not the image of the signature) as the signer executes handwriting in a pattern ingrained early in life.
Over the last 15 years, our research team at NJIT has developed a gun safety system based on a novel behavioral biometric called Dynamic Grip Recognition™ (DGR). The team demonstrated that changes over time to the pressure pattern created on the grip of a handgun as one counter-braces the force of trigger pull were individual to the user, reproducible and measurable.
Our prototype detects grip patterns during the first 1/10th of a second of trigger pull and unlocks the weapon with no apparent lag to the shooter. Because DGR works during trigger pull of a properly held weapon, the approach can also reduce accidental firings during mishandling of a loaded weapon.
The author describes personalized weapons research at NJIT.
Reliability – can I trust you?
Reliability is always a concern raised in discussions of electronic gun safety systems.
The interior of a firing weapon is not a friendly environment for electronics, but there is now a sufficient history of ruggedized circuitry that failure rates of the underlying electronic hardware are orders of magnitude less than the predicted failure rates of the mechanical weapon (somewhere between 1 in 1000 and 1 in 10,000 depending on the precision and quality of the weapon).
Power is clearly a concern here, too. But advances in microprocessor technology and battery storage that have been driven by smart phones and portable electronics remove this issue as a show stopper. Motion detection and wake-up software can reduce battery drain during storage. Integrating the power supply to the ammunition clip and even charging by mechanical cycling are all ways to address power loss as a mode of failure.
In biometric systems, there is another element to consider: failure of the identification algorithm. Those are false negatives in which a rightful user is not recognized, or false positives in which an impostor is wrongly authenticated. The recognition rates for fingerprint detectors have been claimed to be as high as 99.99 percent (1 in 10,000 failure rate).
As the array of sensor technologies grows, one might expect a multisensor or multispectral approach to be the ultimate choice for biometric-based systems. These have the advantage of multiplying reliability rates when independent measures are used. For example, a fingerprint sensor with a 1-in-10,000 failure rate, coupled with a dynamic grip recognition with a failure rate of 1 in 1000, would produce a combined reliability of 1 in 10,000 x 1000 or 1 in 10,000,000.
Will we ever be able to buy one?
Throughout the 20-year-long discussion of “smart guns,” the topic has been a lightning rod for debate between pro- and anti-gun lobbies. But too often, there isn’t substantive knowledge of the underlying technologies, their appropriate use and their design limitations.
Personalized weapons technology can make a contribution to reducing death and injury from accidental or unauthorized weapons use. It is not a panacea – the technology can’t stop shootings like Virginia Tech, Aurora or Sandy Hook, where lawfully purchase weapons were used. But it can be an option for gun buyers to ensure their weapons never fall into the wrong hands.
The existing platforms show that smart guns are not science fiction and could be a commercial reality much sooner than later. A recent survey by the NIJ identified 13 different personalized weapon systems, at least three of which were deemed to be in commercial preproduction. Obama’s initiative could be an important step to accelerate development and promote private sector investment necessary to mature these technologies to the point of reliability and affordability that will spur consumer adoption.
Donald Sebastian, Professor of Chemical, Biological and Pharmaceutical Engineering, New Jersey Institute of Technology
This article was originally published on The Conversation. Read the original article. Follow all of the Expert Voices issues and debates — and become part of the discussion — on Facebook, Twitter and Google +. The views expressed are those of the author and do not necessarily reflect the views of the publisher. This version of the article was originally published on Live Science.